November 4 2014 Tuesday
The Domino fixes for POODLE and TLS, you may not be done yet
Update - IGNORE THIS POST, go read http://blog.darrenduke.net/Darren/DDBZ.nsf/dx/tls-1.2-in-domino-and-the-settings-i-use.htm instead
As you read elsewhere IBM have finally addressed POODLE and TLS 1.0 are now available for for these releases on all platforms, 9.0.1 FP2, 9.0, 8.5.3 FP6, 8.5.2 FP4 and 8.5.1 FP5.
Now just implementing these fixes may not completely protect you, (thinking BEAST attack here) unless you also disable both AES ciphers in Domino. Basically these are the two ciphers you want enabled:
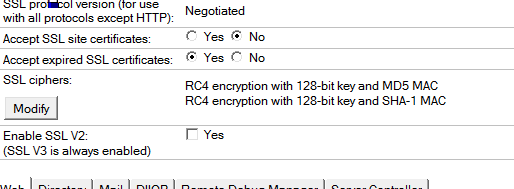
It's worth pointing out that with the TLS1.0 fix IBM also addressed a long time pet peeve of mine, low quality ciphers:
A good move but you still should really disable 128bit AES ciphers too. Indeed if you have 40 or 56 bit ciphers enabled then the Domino console throws this out:
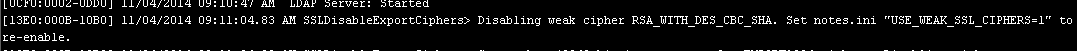
If you *do* need to enable these low quality ones then you are doing something really, really wrong.
Disable the AES ones and you may just end up with a "B" grade at https://www.ssllabs.com/ssltest/index.html (the server below was also upgraded to SHA2)
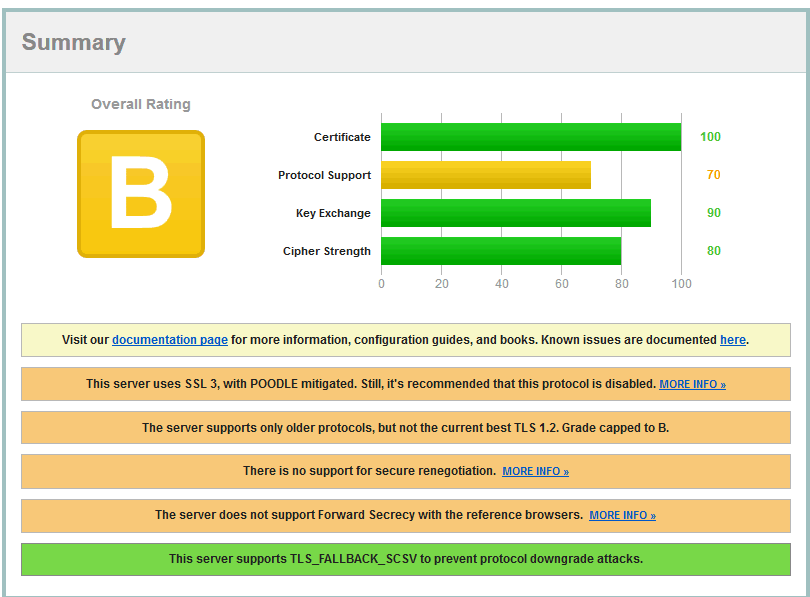
If you want an "A" use my proxy server as Apache does support TLS1.2.
Now, IBM, you have brought us into 1999 with TLS 1.0, when do we get to the heady heights of 2008 and TLS 1.2? All kidding aside IBM have shown here that they can *still* do amazingly good work in a pretty short period of time. Once the SHTF it took less than 90 days for this to be addressed. Hopefully this is the shape of things to come and this sense of urgency for security will remain and not be left on the shelf until the next end-of-the-world-security-failure scenario.
I won't hold my breath for TLS 1.2 support, but I will cross my fingers.
As you read elsewhere IBM have finally addressed POODLE and TLS 1.0 are now available for for these releases on all platforms, 9.0.1 FP2, 9.0, 8.5.3 FP6, 8.5.2 FP4 and 8.5.1 FP5.
Now just implementing these fixes may not completely protect you, (thinking BEAST attack here) unless you also disable both AES ciphers in Domino. Basically these are the two ciphers you want enabled:
It's worth pointing out that with the TLS1.0 fix IBM also addressed a long time pet peeve of mine, low quality ciphers:
Removed support:
- SSLv2
- SSL renegotiation has been disabled
- All weak (<128 bits) cipher suites have been disabled
A good move but you still should really disable 128bit AES ciphers too. Indeed if you have 40 or 56 bit ciphers enabled then the Domino console throws this out:
If you *do* need to enable these low quality ones then you are doing something really, really wrong.
Disable the AES ones and you may just end up with a "B" grade at https://www.ssllabs.com/ssltest/index.html (the server below was also upgraded to SHA2)
If you want an "A" use my proxy server as Apache does support TLS1.2.
Now, IBM, you have brought us into 1999 with TLS 1.0, when do we get to the heady heights of 2008 and TLS 1.2? All kidding aside IBM have shown here that they can *still* do amazingly good work in a pretty short period of time. Once the SHTF it took less than 90 days for this to be addressed. Hopefully this is the shape of things to come and this sense of urgency for security will remain and not be left on the shelf until the next end-of-the-world-security-failure scenario.
I won't hold my breath for TLS 1.2 support, but I will cross my fingers.
Darren Duke
|
November 4 2014 03:49:27 PM
|
domino tls security
|
Discussion for this entry is now closed.
Comments (4)
You are not wrong about "modern clients", but with IE 8 (yes EIGHT!) being the 2nd most popular browser (currently 17% market share at http://www.netmarketshare.com/browser-market-share.aspx?qprid=2&qpcustomd=0) I would suggest that un-modern clients are still far too prevalent.
This is not an IE fix, this is a Windows SChannel fix.





I don't think disabling AES is a good idea. Most modern clients have BEAST record splitting workarounds, and IE11 tries to connect without RC4 by default.