June 1 2021 Tuesday
Ransomware Prevention Part 4 - Endpoint Protection aka Antivirus
Part 4 - Endpoint Protection
See here for the entire series of posts, if you are just stumbling onto these posts.
As I said in part one, these post are supposed to be helpful in giving you meaningful useful advice to prevent ransomware.
Antivirus, or more correctly called endpoint protection these days, is the one item that organization rarely change out. And when they do it's often because they just got hit and their current endpoint protection solution, did not, in fact, offer any protection to any of their endpoints. Or even worse the solution didn't report it until the point of no recovery. These organizations could have saved themselves a whole lot of hurt if only they had a policy in place to evaluate these solutions every two to three years. You then have to be willing and able to switch to whatever solution best fits their needs. If you've been running the same solution for over 4 years and have not looked at the competition you are doing it wrong.
Let's get this out of the way right now, no one solution is guaranteed to stop everything. However the earlier the detection the better off you will be. The solution you choose can be the difference between a report of a stopped threat or a 2-6 month hell of restoring backups (backups are covered in a later post) or being caught in the hellscape that is awaiting those who pay up. So how does one chose a solution that is your last line of technical defence, the last skin on the onion? Especially now what there is EDR, EDTR and many other acronyms flying about? As with most other choices in life you use data.
There are independent test sites out there that will take a vendor's solution out for a range test. The vendor sometime suggests settings these test should have, or not. Just depends. Now, some vendors don't want to play in the test range scenarios, so if you are looking at one of those you will have to look elsewhere for your data. My personal go to site for these tests is AV Comparatives and AV-Test (you want the business/enterprise tests, not the consumer.....different game). For those who want really, really detailed reporting (although less overall solutions are reviewed) look no further than MRG Effitas and their 40 page reports.
Long before you hit the independent sites you will already want your list of criteria (and stopping everything with zero overhead and no false positives is not a criteria, that's called a dream). Something along the lines of this:
Now, the above may not be your list (price maybe of no concern for example), but write down and rank your objectives for your replacement solution. Now for a little secret, this is pretty much my list, so I'm going to go over each point one at a time:
Easy to Use
If it's not easy to use, it's not easy to secure. By that I mean for the most part you want the configuration and management simple enough to do in-house (unless price is no issue). I have the same rule for firewalls, it's it too complex for on-premises folks to understand can you really guarantee your security?
Low system overhead
The one that no one thinks about until you've already deployed it and what causes you to disable features. Now, no one wants a slow protection solution, but many get one.
High long-term score on independent test sites
Or whatever site you trust the best. Each vendor can have a good month or quarter. Even a wrong watch is correct twice a day. What you are after is a long-term trend of excellent scores. When I say independent test site I do not mean a magic quadrant or some other somewhat meaningless mechanism that offers no real-world efficacy results.
Reasonably priced
Usually in relation to the vendor you are replacing. Sometimes not. Most vendors have competitive SKUs that offer significant discounts when moving to their products. If money is absolutely no object I'll save you a lot of reading, go look at CrowdStrike.
Prefer cloud to on-prem management
When you get ransomwared you could also lose domain controllers and the very security management servers and manage you endpoint protection solutions. If your solution relies solely with an on-prem management server and it got nuked now what do you do? You may even have that management server using AD SSO. So now you need a DC restored to even get to manage your endpoints. As you can imagine, in the heat of a recovery operation (meaning can you recovery or are you likely to have to pay?) the less you have to have online or restore in the heat of the moment the better off you are. If you had cloud management, this type of hellish scenario is moot. Another reason to embrace cloud for this is AI and sheer amount of samples submitted. This significantly reduces the time to updated definitions.
With the above in mind off I trot to my trusted independent site. I'll use AV Comparatives for this as their charts are easier to read.
Types of tests
These sites don't only measure efficacy, but some also measure performance (remember, you do not want your new shiny all singing, all dancing solution to be a boat anchor). This saves quite the step when attempting to do a benchmarking bake-off. AV-Test has some even better breakdowns of the performance:
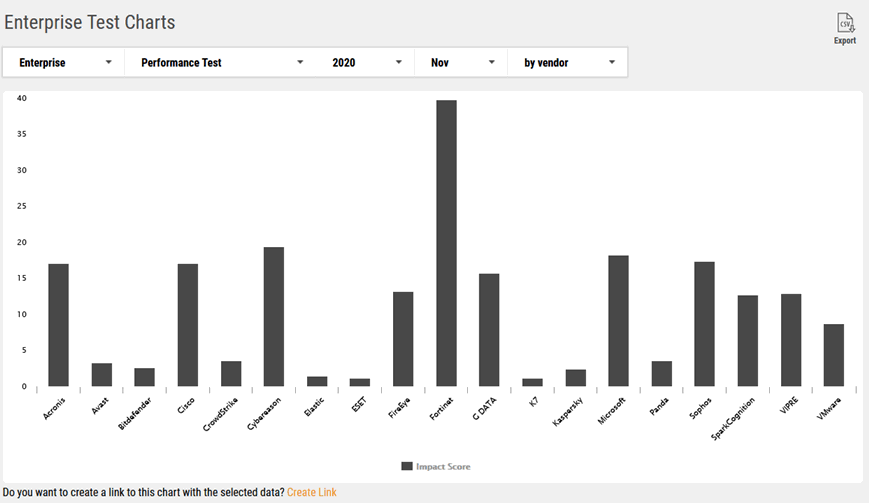
The performance chart is quite eye-popping for than no other reason than Fortinet. The other one I see a lot, and hence hear a lot of grumbling is Sophos from a performance stand-point. Anything >7 is doing a whole lot of stuff:
From a real-world protection view things appear somewhat close. This is mainly due to the fact that any vendor not hitting >95% has little reason to submit to this kind of test. This does not mean that just because a vendor is not on here (Webroot and Sentinel One are two phenomenal solutions that are not here) and that you should immediately start a project to change them out. Not at all, but least go find out how effective your current solution is in relation to other solutions. Then act appropriately.
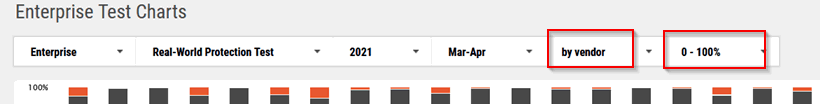
So to get a better view of the contenders you will need to do some tweaking to make the charts easier to read: Specifically, change these settings:
With those adjusted it now shows a much clearer indication of the efficacy:
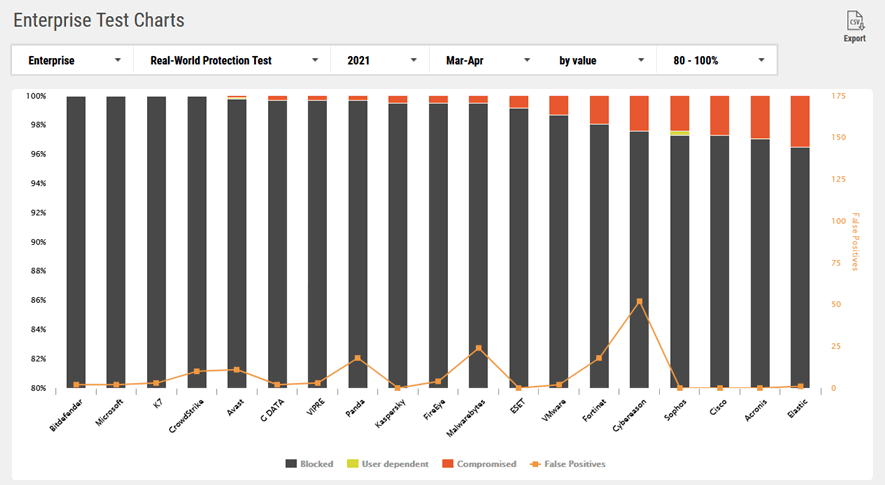
OK, now were getting somewhere. Some points from the above chart, albeit a single point in time:
The above is just a snapshot, by changing the month/year the results can swing wildly (CrowdStrike and FireEye anyone?):
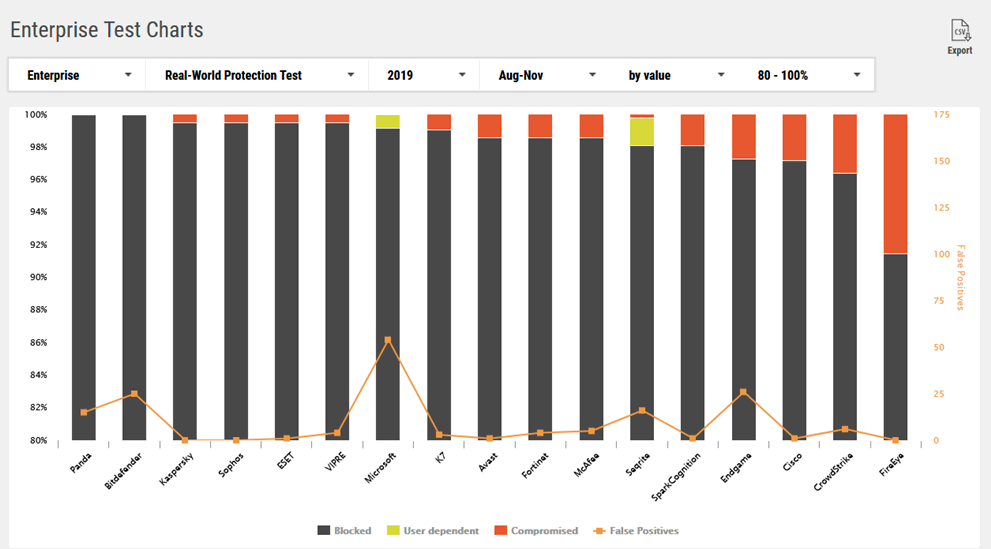
Each and every reporting period will be slightly different (remember, one solution won't stop everything immediately) but patterns do emerge. While some seesaw wildly, some are always in the top 50% others are always in the bottom 50%. Maybe now I have my top three or four contenders, so it maybe time to see what the other sites say. You're on your own here, you now know what to do.
Features
There are now a plethora of features. Some solutions offer patching (usually as an add-on and patching is not vulnerability scanning, right?). Most will now do EDR and some will do ransomware protection (YMMV), common misconfigurations and process recording with their higher end versions, Some can even take screen shots when the device (read user) does something that triggers it. You want behavior analysis (sometimes called heuristics). As an example if a Word document suddenly decides to send 100's of emails is that normal (hint, it's not normal)? Also be sure to RTFM every few months, especially if you are on a cloud managed solution. They are adding features all the time and not all are enabled by default.
As an example here is Bitdefender GravityZone Ultra's process execution track when something suspicious happens and misconfigured systems screens:
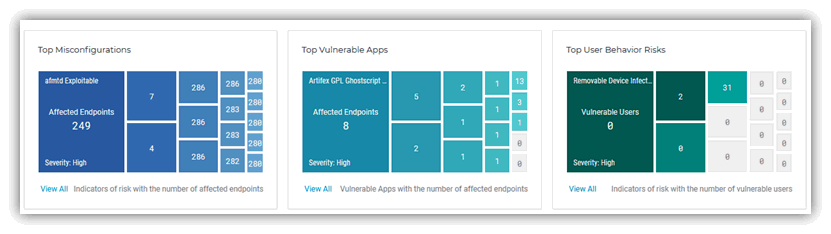
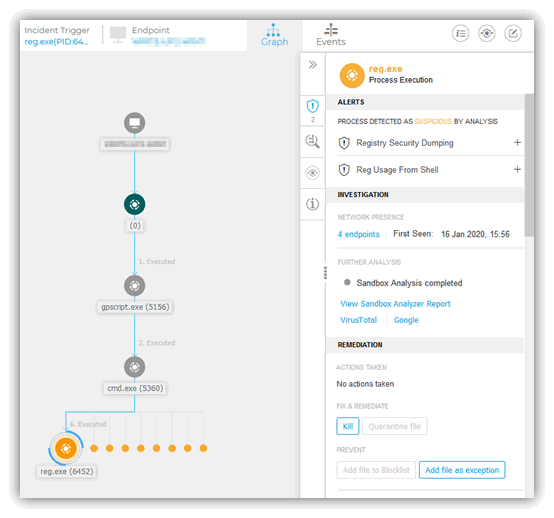
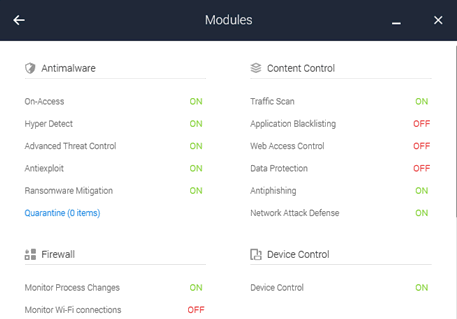
Here is an example of all the modules currently available for a desktop/laptop when using BitDefender GravityZone Ultra which goes to show the sheer number of features some of these products now have:
What these solutions won't do
While I said ease of use and low overhead was a desirable attributes, these solutions do not configure themselves. You need to slowly tighten down the protection settings to ensure you are getting the best possible protection. All security is a knife edge and endpoint protection is no different. A fully secure endpoint is one that is not connected to a power outlet, but it's level of productivity is affected adversely. While it's not a zero sum game it's still something we have to be cognizant of. And even a relatively fast solution can be made slow by not paying attention. The number of places I see who turned on a new protection feature only to disable it again after user complaints is astronomical.
An example of configuration.....Most solutions can do signing certificate exemptions (I'll also talk at length about signing certs in the GPO post). However when whitelisting most will simply enter a path. So when Microsoft Teams doesn't work with their new endpoint solution (enter your own joke here about Teams being a virus), and while entering a path is often the simplest way to make it work (with something like %userprofile%\appdata\Teams\*) this is also opening up a whole host of issues. It's not like the hackers don't know world + dog use Teams. It's not like the hackers don't know the path that Teams installs in (that somewhat flaunts Microsoft's own programming guidelines). But if you just whitelisted the entire Teams folder and a hacker drops Emotet or some other dropper in there what now happens? Right, a no good very bad day is awaiting you sometime in the future. So whitelist your endpoint security exceptions with signing certificates and not paths.
Conclusion
While I can't assist you in the the decision you are now mulling over after reading this (this is not a paying engagement, but feel free to contact Lisa if that floats your boat), you now at least know how to cut through the sales person talk and find out what really are the best of the best in terms of endpoint protection.
See here for the entire series of posts, if you are just stumbling onto these posts.
As I said in part one, these post are supposed to be helpful in giving you meaningful useful advice to prevent ransomware.
Your last line of technical defence is often your most ignored.
Antivirus, or more correctly called endpoint protection these days, is the one item that organization rarely change out. And when they do it's often because they just got hit and their current endpoint protection solution, did not, in fact, offer any protection to any of their endpoints. Or even worse the solution didn't report it until the point of no recovery. These organizations could have saved themselves a whole lot of hurt if only they had a policy in place to evaluate these solutions every two to three years. You then have to be willing and able to switch to whatever solution best fits their needs. If you've been running the same solution for over 4 years and have not looked at the competition you are doing it wrong.
Let's get this out of the way right now, no one solution is guaranteed to stop everything. However the earlier the detection the better off you will be. The solution you choose can be the difference between a report of a stopped threat or a 2-6 month hell of restoring backups (backups are covered in a later post) or being caught in the hellscape that is awaiting those who pay up. So how does one chose a solution that is your last line of technical defence, the last skin on the onion? Especially now what there is EDR, EDTR and many other acronyms flying about? As with most other choices in life you use data.
There are independent test sites out there that will take a vendor's solution out for a range test. The vendor sometime suggests settings these test should have, or not. Just depends. Now, some vendors don't want to play in the test range scenarios, so if you are looking at one of those you will have to look elsewhere for your data. My personal go to site for these tests is AV Comparatives and AV-Test (you want the business/enterprise tests, not the consumer.....different game). For those who want really, really detailed reporting (although less overall solutions are reviewed) look no further than MRG Effitas and their 40 page reports.
Long before you hit the independent sites you will already want your list of criteria (and stopping everything with zero overhead and no false positives is not a criteria, that's called a dream). Something along the lines of this:
- Easy to use, not a lot of professional services required.
- Low system overhead, can't cause significant slowdowns of systems.
- High long-term score on independent test sites..
- Reasonably priced.
- Prefer cloud to on-prem for management.
Now, the above may not be your list (price maybe of no concern for example), but write down and rank your objectives for your replacement solution. Now for a little secret, this is pretty much my list, so I'm going to go over each point one at a time:
Easy to Use
If it's not easy to use, it's not easy to secure. By that I mean for the most part you want the configuration and management simple enough to do in-house (unless price is no issue). I have the same rule for firewalls, it's it too complex for on-premises folks to understand can you really guarantee your security?
Low system overhead
The one that no one thinks about until you've already deployed it and what causes you to disable features. Now, no one wants a slow protection solution, but many get one.
High long-term score on independent test sites
Or whatever site you trust the best. Each vendor can have a good month or quarter. Even a wrong watch is correct twice a day. What you are after is a long-term trend of excellent scores. When I say independent test site I do not mean a magic quadrant or some other somewhat meaningless mechanism that offers no real-world efficacy results.
Reasonably priced
Usually in relation to the vendor you are replacing. Sometimes not. Most vendors have competitive SKUs that offer significant discounts when moving to their products. If money is absolutely no object I'll save you a lot of reading, go look at CrowdStrike.
Prefer cloud to on-prem management
When you get ransomwared you could also lose domain controllers and the very security management servers and manage you endpoint protection solutions. If your solution relies solely with an on-prem management server and it got nuked now what do you do? You may even have that management server using AD SSO. So now you need a DC restored to even get to manage your endpoints. As you can imagine, in the heat of a recovery operation (meaning can you recovery or are you likely to have to pay?) the less you have to have online or restore in the heat of the moment the better off you are. If you had cloud management, this type of hellish scenario is moot. Another reason to embrace cloud for this is AI and sheer amount of samples submitted. This significantly reduces the time to updated definitions.
With the above in mind off I trot to my trusted independent site. I'll use AV Comparatives for this as their charts are easier to read.
Types of tests
These sites don't only measure efficacy, but some also measure performance (remember, you do not want your new shiny all singing, all dancing solution to be a boat anchor). This saves quite the step when attempting to do a benchmarking bake-off. AV-Test has some even better breakdowns of the performance:
The performance chart is quite eye-popping for than no other reason than Fortinet. The other one I see a lot, and hence hear a lot of grumbling is Sophos from a performance stand-point. Anything >7 is doing a whole lot of stuff:
From a real-world protection view things appear somewhat close. This is mainly due to the fact that any vendor not hitting >95% has little reason to submit to this kind of test. This does not mean that just because a vendor is not on here (Webroot and Sentinel One are two phenomenal solutions that are not here) and that you should immediately start a project to change them out. Not at all, but least go find out how effective your current solution is in relation to other solutions. Then act appropriately.
So to get a better view of the contenders you will need to do some tweaking to make the charts easier to read: Specifically, change these settings:
With those adjusted it now shows a much clearer indication of the efficacy:
OK, now were getting somewhere. Some points from the above chart, albeit a single point in time:
- Microsoft usually does well. But could I sleep well at night having all my eggs in *that* basket?
- Kaspersky is usually a lot higher. Proving that even one of the best efficacy solutions can have a bad month/quarter.
- Be aware that a vendor may appear in the efficacy but not the performance charts (Malwarebytes). Test performance of that solution accordingly.
- Webroot and Sentinel One are absent.
- VMware is Carbon Black.
- Kaspersky cannot be used in US government agencies. If this is you, disregard this vendor. Kaspersky is like Microsoft, if you can sleep well at night using it, have at it.
- Neither McAfee or Symantec are anywhere to be seen. I'll leave you to jump to your own conclusion about these absences.
The above is just a snapshot, by changing the month/year the results can swing wildly (CrowdStrike and FireEye anyone?):
Each and every reporting period will be slightly different (remember, one solution won't stop everything immediately) but patterns do emerge. While some seesaw wildly, some are always in the top 50% others are always in the bottom 50%. Maybe now I have my top three or four contenders, so it maybe time to see what the other sites say. You're on your own here, you now know what to do.
Features
There are now a plethora of features. Some solutions offer patching (usually as an add-on and patching is not vulnerability scanning, right?). Most will now do EDR and some will do ransomware protection (YMMV), common misconfigurations and process recording with their higher end versions, Some can even take screen shots when the device (read user) does something that triggers it. You want behavior analysis (sometimes called heuristics). As an example if a Word document suddenly decides to send 100's of emails is that normal (hint, it's not normal)? Also be sure to RTFM every few months, especially if you are on a cloud managed solution. They are adding features all the time and not all are enabled by default.
As an example here is Bitdefender GravityZone Ultra's process execution track when something suspicious happens and misconfigured systems screens:
Here is an example of all the modules currently available for a desktop/laptop when using BitDefender GravityZone Ultra which goes to show the sheer number of features some of these products now have:
What these solutions won't do
While I said ease of use and low overhead was a desirable attributes, these solutions do not configure themselves. You need to slowly tighten down the protection settings to ensure you are getting the best possible protection. All security is a knife edge and endpoint protection is no different. A fully secure endpoint is one that is not connected to a power outlet, but it's level of productivity is affected adversely. While it's not a zero sum game it's still something we have to be cognizant of. And even a relatively fast solution can be made slow by not paying attention. The number of places I see who turned on a new protection feature only to disable it again after user complaints is astronomical.
Turning a feature off is not the answer. Tuning the feature is.
An example of configuration.....Most solutions can do signing certificate exemptions (I'll also talk at length about signing certs in the GPO post). However when whitelisting most will simply enter a path. So when Microsoft Teams doesn't work with their new endpoint solution (enter your own joke here about Teams being a virus), and while entering a path is often the simplest way to make it work (with something like %userprofile%\appdata\Teams\*) this is also opening up a whole host of issues. It's not like the hackers don't know world + dog use Teams. It's not like the hackers don't know the path that Teams installs in (that somewhat flaunts Microsoft's own programming guidelines). But if you just whitelisted the entire Teams folder and a hacker drops Emotet or some other dropper in there what now happens? Right, a no good very bad day is awaiting you sometime in the future. So whitelist your endpoint security exceptions with signing certificates and not paths.
Conclusion
While I can't assist you in the the decision you are now mulling over after reading this (this is not a paying engagement, but feel free to contact Lisa if that floats your boat), you now at least know how to cut through the sales person talk and find out what really are the best of the best in terms of endpoint protection.



