September 16 2015 Wednesday
Supercharge your Domino servers with OCSP Stapling - real go faster stripes
OK, so I know I said IBM were dropping the ball on 9.0.2 but the Domino security team have been knocking the ball out of the park lately (IBM, don't ignore security again.....just saying).
Anyhow, yesterday was HSTS, today I give you OCSP Stapling in Domino. Again the crowds ask, "WTF?"....Via Wikipedia (and, yes a bit yawny....):
OK, that was snoozie....wake up!!!!
What does it do really? Well, it fixes an issue that has been the bane of SSL for at least a decade. See your CA is getting queried every time your SSL'd pages are getting accessed to see if your certificate is valid. It does this using the Online Certificate Status Protocol (OCSP). That takes time. In some cases quite a bit of time, adding apparent latency to you HTTPS applications. This issue can be addressed via OCSP Stapling.
Here's the original OCSP way (images courtesy of https://www.grc.com/revocation/ocsp-must-staple.htm):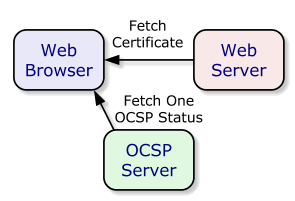
As you can see above, your browser is making two calls to validate your SSL certificate. Once OCSP Stapling is enabled the flow looks like this: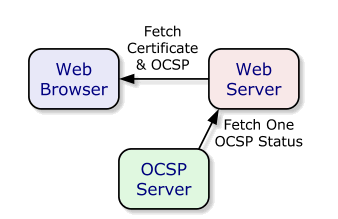
Technically the browser is only making one call. For the mathematically challenged that's a 50% reduction. Not bad right?. So what is happening here?
Well, your web server is now taking responsibility for letting the browser know that your certificate is indeed valid. The browser now has no need to go out to the CA to check the OCSP list. This isn't an issue (I know you think it is, but it isn't) as the server retrieves the OCSP list at regular intervals and obtains a time-stamped, signed OCSP response (Domino does about 8 every hours....I think) and then this response is then added ("stapled" if you will) to the TLS/SSL handshake that happens when the browser and server contact each other for the first time. There are some added security measures with this response that prevent CA fraud from taking place. The only real downside is that a revoked certificate may not been seen as revoked by a client until the next scheduled retrieval of the OCSP list.
If the browser supports OCSP Stapling (I know of no modern browsers that do not, except Apple's Safari) then the browser now has a trusted and verifiable source that your SSL certificate is valid. No need to go out to the OCSP directly. Voila, faster SSL pages loads. In some cases there have been reports of a 30% increase. Any browsers that don't support OCSP Stapling just revert to the old way of check the OCSP itself (the first diagram above). No harm, no foul.
With the release of 9.0.1 FP4 IBM added OCSP Stapling to Domino, however you still have to do some things:
1) Make sure you are running 9.0.1 FP4 or higher.
2) Find out the OCSP URI for you SSL provider. You can see this in you SSL certificate:
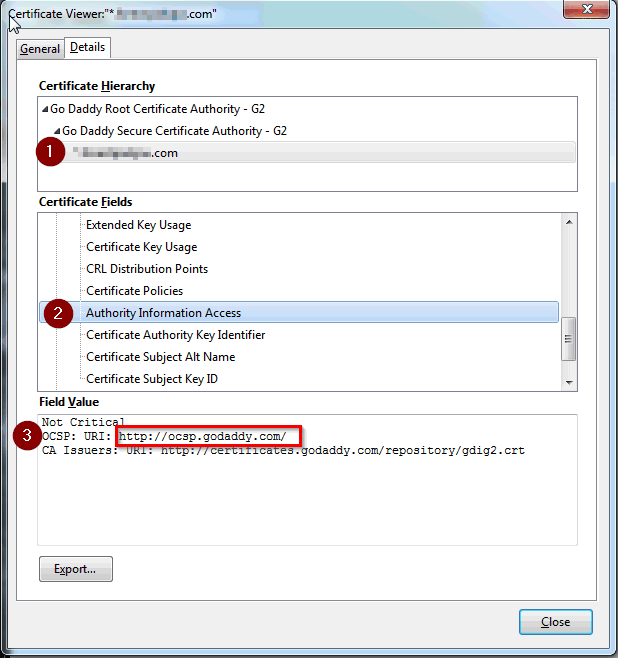
3) Add the following to you server notes.ini:
(note the OCSP_CLOCKSKEW is a number of minutes to allow the time-stamp some leeway if your server and the CA clocks are off a bit. You may or may not need it)
(note2 OCSP_RESPONDER is the URI you see in (2). This may or may not be GoDaddy)
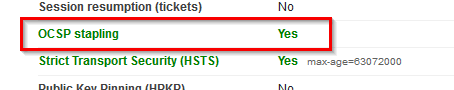
4) Restart the server (a HTTP restart may not suffice) and scan you server with SSL Labs and you should get this:
You can also check via openssl using this command:
If OCSP Stapling is enabled and working you should see something like this:
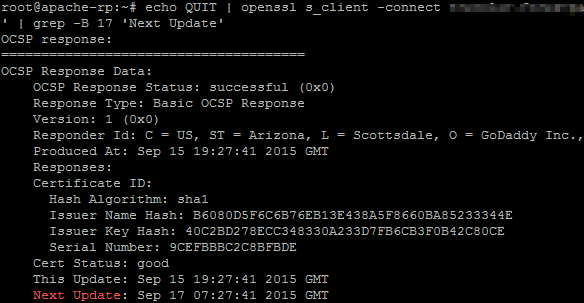
If OCSP Stapling is not working then you get no response.
5) Bask in the glory that you are master of your own universe and now you have a much more responsive Domino server.
Again, kudos to the Domino security team for adding this. Now when can I have 256 bit AES Notes Port encryption? ;)
Anyhow, yesterday was HSTS, today I give you OCSP Stapling in Domino. Again the crowds ask, "WTF?"....Via Wikipedia (and, yes a bit yawny....):
OCSP stapling, formally known as the TLS Certificate Status Request extension, is an alternative approach to the Online Certificate Status Protocol (OCSP) for checking the revocation status of X.509 digital certificates.[1] It allows the presenter of a certificate to bear the resource cost involved in providing OCSP responses by appending ("stapling") a time-stamped OCSP response signed by the CA to the initial TLS Handshake, eliminating the need for clients to contact the CA
OK, that was snoozie....wake up!!!!
What does it do really? Well, it fixes an issue that has been the bane of SSL for at least a decade. See your CA is getting queried every time your SSL'd pages are getting accessed to see if your certificate is valid. It does this using the Online Certificate Status Protocol (OCSP). That takes time. In some cases quite a bit of time, adding apparent latency to you HTTPS applications. This issue can be addressed via OCSP Stapling.
Here's the original OCSP way (images courtesy of https://www.grc.com/revocation/ocsp-must-staple.htm):
As you can see above, your browser is making two calls to validate your SSL certificate. Once OCSP Stapling is enabled the flow looks like this:
Technically the browser is only making one call. For the mathematically challenged that's a 50% reduction. Not bad right?. So what is happening here?
Well, your web server is now taking responsibility for letting the browser know that your certificate is indeed valid. The browser now has no need to go out to the CA to check the OCSP list. This isn't an issue (I know you think it is, but it isn't) as the server retrieves the OCSP list at regular intervals and obtains a time-stamped, signed OCSP response (Domino does about 8 every hours....I think) and then this response is then added ("stapled" if you will) to the TLS/SSL handshake that happens when the browser and server contact each other for the first time. There are some added security measures with this response that prevent CA fraud from taking place. The only real downside is that a revoked certificate may not been seen as revoked by a client until the next scheduled retrieval of the OCSP list.
If the browser supports OCSP Stapling (I know of no modern browsers that do not, except Apple's Safari) then the browser now has a trusted and verifiable source that your SSL certificate is valid. No need to go out to the OCSP directly. Voila, faster SSL pages loads. In some cases there have been reports of a 30% increase. Any browsers that don't support OCSP Stapling just revert to the old way of check the OCSP itself (the first diagram above). No harm, no foul.
With the release of 9.0.1 FP4 IBM added OCSP Stapling to Domino, however you still have to do some things:
1) Make sure you are running 9.0.1 FP4 or higher.
2) Find out the OCSP URI for you SSL provider. You can see this in you SSL certificate:
3) Add the following to you server notes.ini:
SSL_ENABLE_OCSP_STAPLING=1
OCSP_RESPONDER=http://ocsp.godaddy.com
OCSP_CLOCKSKEW=15
(note the OCSP_CLOCKSKEW is a number of minutes to allow the time-stamp some leeway if your server and the CA clocks are off a bit. You may or may not need it)
(note2 OCSP_RESPONDER is the URI you see in (2). This may or may not be GoDaddy)
4) Restart the server (a HTTP restart may not suffice) and scan you server with SSL Labs and you should get this:
You can also check via openssl using this command:
echo QUIT | openssl s_client -connect yourserver.com:443 -status 2> /dev/null | grep -A 17 'OCSP response:' | grep -B 17 'Next Update'
If OCSP Stapling is enabled and working you should see something like this:
If OCSP Stapling is not working then you get no response.
5) Bask in the glory that you are master of your own universe and now you have a much more responsive Domino server.
Again, kudos to the Domino security team for adding this. Now when can I have 256 bit AES Notes Port encryption? ;)
Darren Duke
|
September 16 2015 06:17:34 AM
|
domino security ssl
|





Appreciate this info! IBM Domino 901Fp$ releaso note SPR# DKEN9SLU3Y only mentions SSL_ENABLE_OCSP_STAPLING parameter, not the other two to use in conjunction! Thanks! Works like a charm! I've been trying to solve this for days!