September 25 2020 Friday
ZEROLOGON and why you may not actually be protected
As most will have hopefully read by now the ZEROLOGON vulnerability in Windows (CVE-2020-1472) is pretty wild. Basically by passing Windows netlogon process bypassing a series of zeros to it. Fun times!
Microsoft did issue a patch in their August 2020 updates here https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1472, however I'm skeptical that people actually read the FAQ at the bottom of the article:
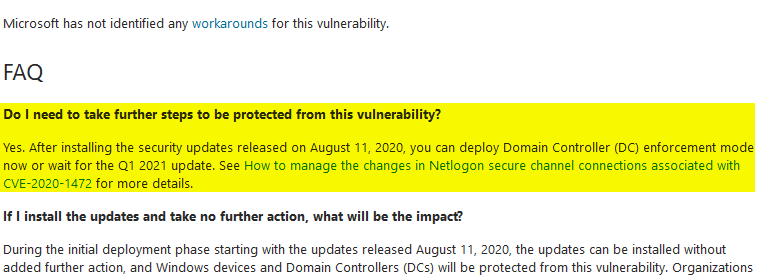
Notice that link in the highlighted section? Here it is https://support.microsoft.com/en-us/help/4557222/how-to-manage-the-changes-in-netlogon-secure-channel-connections-assoc
Which leads us to this nugget:
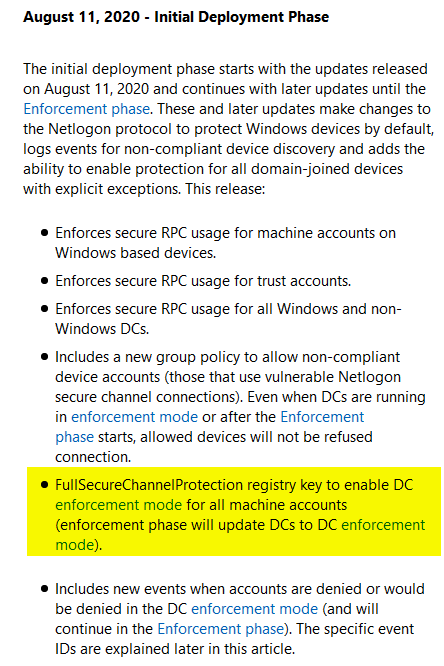
So your Domain Controllers are not fully protected? Admittedly this is a pretty confusing list of bullet points but it does seem to suggest the patch reports as opposed to enforces non-Windows machines. My assumption seems to be backed up by this paragraph below that mentions enforcement will being with the February 2021 patch Tuesday:
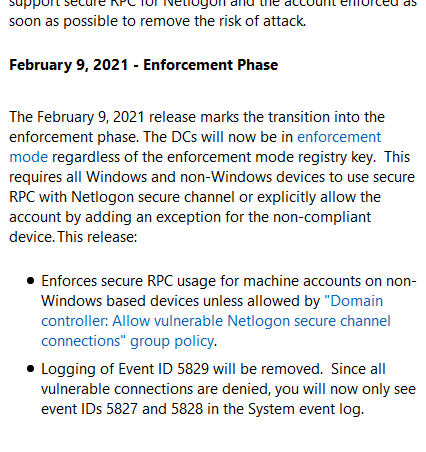
OK, so you installed the patch and your secure right? From Windows devices? Looks like. From non-Windows? I don't believe so unless you add this registry entry otherwise you are flying pants down until February when Microsoft will do it for you:
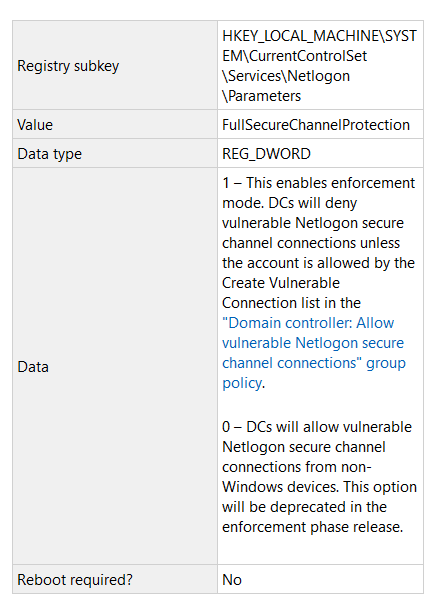
Microsoft did issue a patch in their August 2020 updates here https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1472, however I'm skeptical that people actually read the FAQ at the bottom of the article:
Notice that link in the highlighted section? Here it is https://support.microsoft.com/en-us/help/4557222/how-to-manage-the-changes-in-netlogon-secure-channel-connections-assoc
Which leads us to this nugget:
So your Domain Controllers are not fully protected? Admittedly this is a pretty confusing list of bullet points but it does seem to suggest the patch reports as opposed to enforces non-Windows machines. My assumption seems to be backed up by this paragraph below that mentions enforcement will being with the February 2021 patch Tuesday:
OK, so you installed the patch and your secure right? From Windows devices? Looks like. From non-Windows? I don't believe so unless you add this registry entry otherwise you are flying pants down until February when Microsoft will do it for you:



