January 15 2018 Monday
How to prevent ROBOT (Return Of Bleichenbacher’s Oracle Threat) on Domino servers
Last month, in December 2017 a new (well old, but new) vulnerability was discovered in TLS, the ROBOT attack (Return Of Bleichenbacher's Oracle Threat) and yes, your Domino servers are probably susceptible to it. To avoid re-posting everything from that article go read it them come back.
Your back? OK. So you need to disable any and all RSA encryption ciphers. So here goes (all tests were done on a 9.0.1 FP9 server).....
Before a custom SSLCipherSpec:
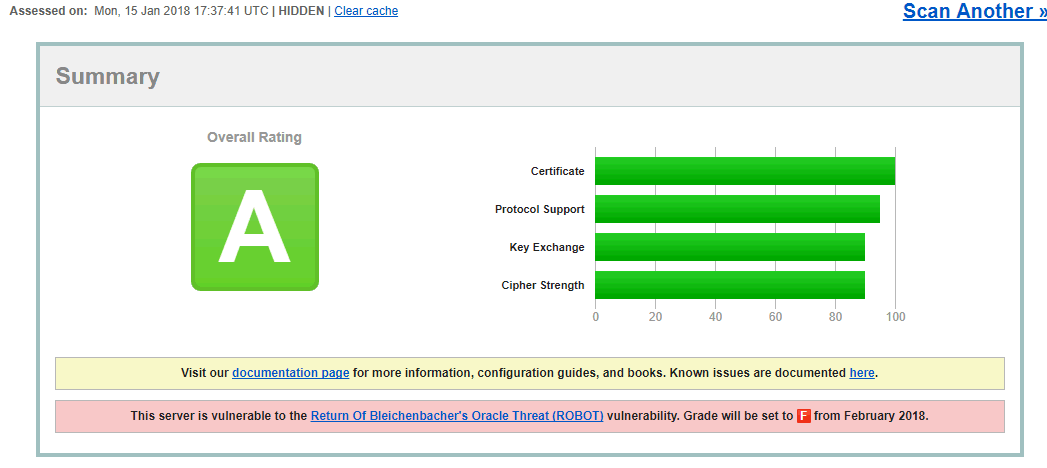
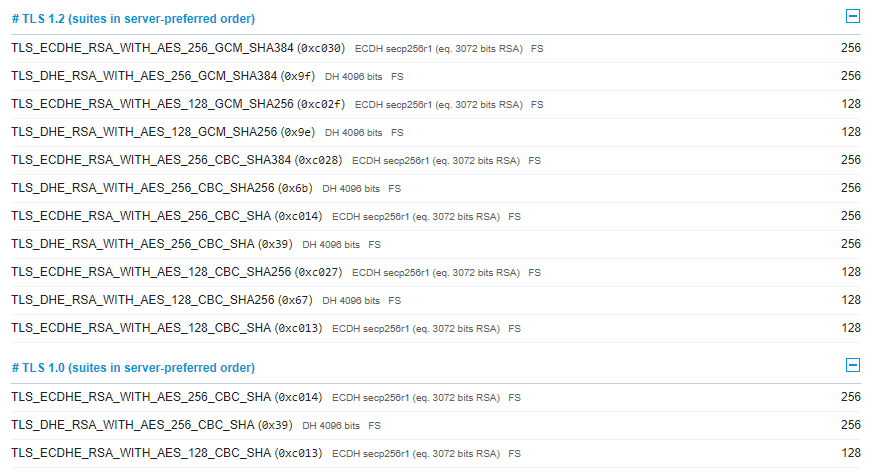
If you look at the ciphers, sure enough there are RSA ciphers in there (TLS_RSA_xxxxxx) for both TLS 1.2 and TLS 1.0 respectively:
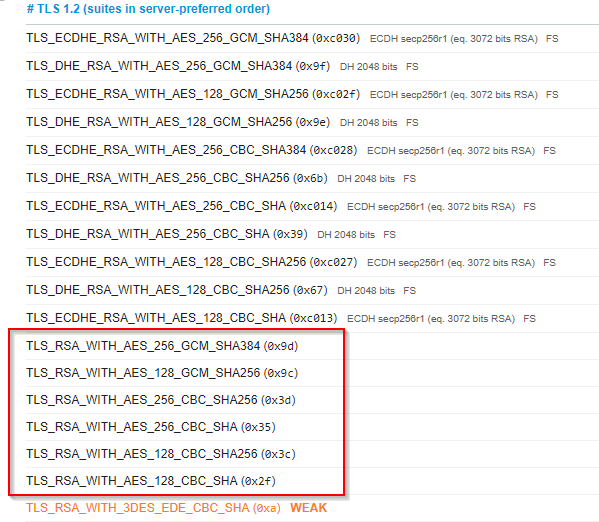
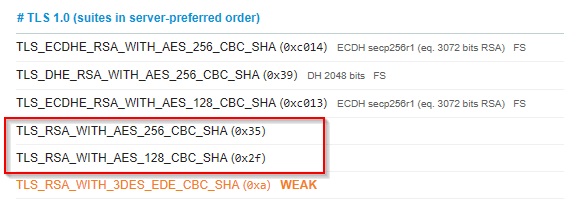
OK, Houston we have a problem. To rectify it use this SSLCipherSpec
C030009FC02F009EC028006BC0140039C0270067C013C0140039C013
Note, I added this via the Domino Console):
set config SSLCIPHERSPEC= C030009FC02F009EC028006BC0140039C0270067C013C0140039C013
Results of the SSL Test after restarting HTTP:
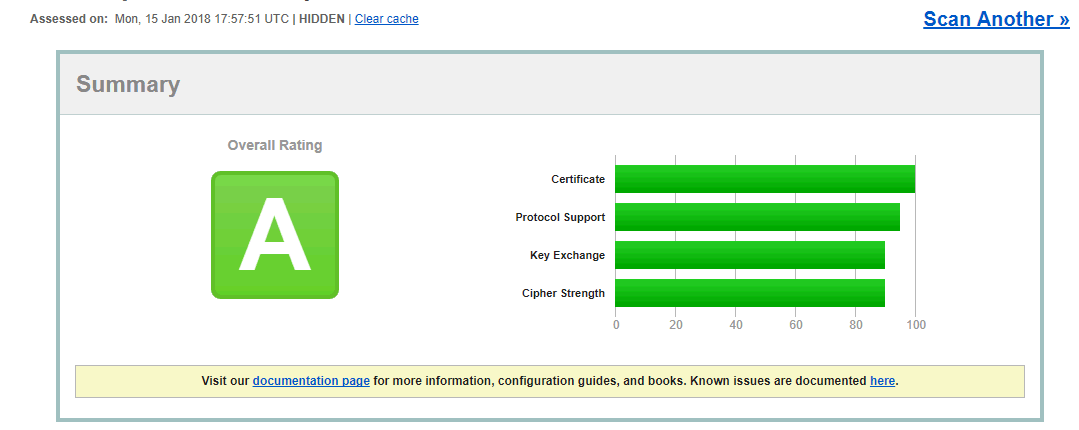
And the errant ciphers are gone:
Your back? OK. So you need to disable any and all RSA encryption ciphers. So here goes (all tests were done on a 9.0.1 FP9 server).....
Before a custom SSLCipherSpec:
If you look at the ciphers, sure enough there are RSA ciphers in there (TLS_RSA_xxxxxx) for both TLS 1.2 and TLS 1.0 respectively:
OK, Houston we have a problem. To rectify it use this SSLCipherSpec
C030009FC02F009EC028006BC0140039C0270067C013C0140039C013
Note, I added this via the Domino Console):
set config SSLCIPHERSPEC= C030009FC02F009EC028006BC0140039C0270067C013C0140039C013
Results of the SSL Test after restarting HTTP:
And the errant ciphers are gone:
Darren Duke
|
January 15 2018 12:51:20 PM
|
domino domino security security
|





Thanks Darren - I picked this up last week and was wondering what IBM's response would be.
It is a particular shame when a fix is readily available using existing Domino functionality searching for +SSLCIPHERSPEC +ibm +domino +Bleichenbacher's gives no IBM technote results.